Quick Brief
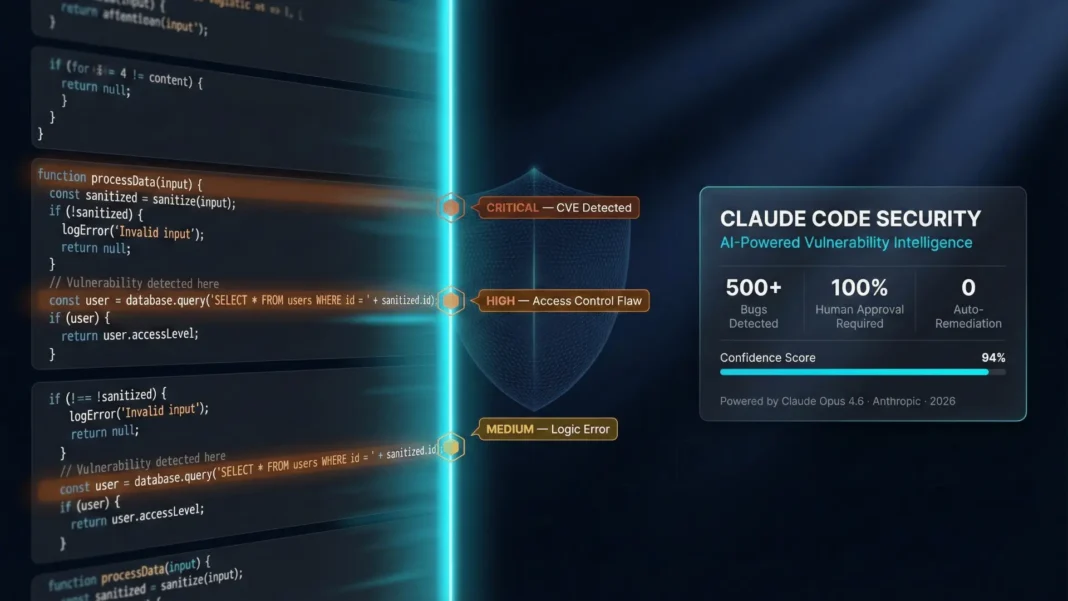
- Claude Code Security scans codebases for vulnerabilities and suggests targeted patches for human review
- Anthropic’s team found 500+ bugs in open-source code that went undetected for decades despite years of expert review
- Every finding passes a multi-stage adversarial verification pass Claude challenges its own results before surfacing them
- Available now in limited research preview for Enterprise and Team customers; open-source maintainers get free, expedited access
Security teams know the problem: too many vulnerabilities, not enough people, and existing tools that only catch what they already know to look for. Anthropic launched Claude Code Security on February 20, 2026 a capability built directly into Claude Code on the web that reads and reasons through codebases like a human security researcher, not a rule matcher. Using Claude Opus 4.6, Anthropic’s own team found over 500 vulnerabilities in production open-source code that had gone undetected for decades, despite years of dedicated expert review. This is how it works, who can access it, and what it means for security teams right now.
What Claude Code Security Actually Does
Static analysis the DevSecOps standard is typically rule-based, matching code against known vulnerability patterns. It catches common issues like exposed passwords or outdated encryption, but consistently misses more complex vulnerabilities: flaws in business logic or broken access control that require understanding how the full system operates.
Claude Code Security takes a different approach. Rather than scanning for known patterns, it reads and reasons about code the way a human security researcher would understand how components interact, tracing how data moves through an application, and catching complex vulnerabilities that rule-based tools miss. Because it is built on Claude Code, teams can review findings and iterate on fixes within the tools they already use.
What does Claude Code Security do?
Claude Code Security scans codebases for security vulnerabilities and suggests targeted patches for human review. Rather than matching known patterns like traditional static analysis tools, it reads and reasons about code the way a human security researcher would tracing data flows, understanding component interactions, and catching complex vulnerabilities including business logic flaws and broken access control.
The Multi-Stage Verification Engine
Every finding goes through a multi-stage verification process before it reaches an analyst. Claude re-examines each result, attempting to prove or disprove its own findings and filter out false positives an adversarial self-check built into the workflow before anything surfaces.
Validated findings appear in the Claude Code Security dashboard, where teams can review them, inspect the suggested patches, and approve fixes. Claude provides both a severity rating and a confidence rating for each finding. Nothing is applied without human approval: Claude Code Security identifies problems and suggests solutions, but developers always make the call.
How findings reach a developer:
- Claude scans the codebase, understanding context and tracing data flows across files
- An adversarial verification pass challenges each finding Claude attempts to disprove its own result before surfacing
- Confirmed findings receive a severity rating so teams can prioritize the most critical issues first
- Each finding also carries a confidence rating to help teams assess context-dependent nuances
- Developer inspects the suggested patch in the dashboard and approves or rejects no automated remediation, no exceptions
The 500+ Bug Discovery: What Testing Actually Found
Claude Code Security builds on more than a year of research into Claude’s cybersecurity capabilities. Anthropic’s Frontier Red Team stress-tested these abilities systematically: entering Claude in competitive Capture-the-Flag events, partnering with Pacific Northwest National Laboratory to experiment with using AI to defend critical infrastructure, and refining Claude’s ability to find and patch real vulnerabilities in code.
Using Claude Opus 4.6, the team found over 500 vulnerabilities in production open-source codebases bugs that had gone undetected for decades, despite years of expert review. Anthropic is currently working through triage and responsible disclosure with the affected maintainers, and plans to expand its security work with the open-source community.
How many vulnerabilities did Claude Code Security find in open-source code?
Using Claude Opus 4.6, Anthropic’s Frontier Red Team found over 500 vulnerabilities in production open-source codebases. These bugs had gone undetected for decades despite years of expert review. Anthropic is working through triage and responsible disclosure with affected maintainers as of February 2026.
Rule-Based Tools vs. Reasoning-Based Scanning
Traditional static analysis tools are rule-based they match code against known vulnerability patterns. This approach reliably catches well-documented issues like exposed passwords and outdated encryption. Where it falls short is on context-dependent vulnerabilities: subtle business logic flaws, broken access control spanning multiple components, and data flow issues that require understanding the whole application, not just a pattern in a single file.
Claude Code Security removes that ceiling by reasoning through code rather than scanning it against rules. The tool understands context, traces data flows across files, and identifies complex multi-component vulnerability patterns that traditional scanners are not designed to detect. Anthropic built the same defensive capabilities it uses to secure its own systems into a tool now available to external teams.
| Dimension | Claude Code Security | Rule-Based Static Analysis |
|---|---|---|
| Detection approach | Reasoning through code like a human researcher | Pattern-matching against known vulnerability signatures |
| Business logic flaws | Detects context-dependent issues | Typically missed |
| Broken access control | Traces multi-component interactions | Limited to documented patterns |
| Exposed passwords / outdated encryption | Detects | Detects |
| False positive handling | Multi-stage adversarial self-verification | Depends on rule precision |
| Human approval required | Yes mandatory for every fix | Varies by tool |
| Access model | Limited research preview Enterprise, Team, OSS | Generally available tools vary |
How does Claude Code Security differ from traditional static analysis tools?
Traditional static analysis tools are rule-based they match code against known vulnerability patterns and reliably catch documented issues like exposed passwords. Claude Code Security reasons through code instead, understanding component interactions and tracing data flows to detect complex vulnerabilities like business logic flaws and broken access control that rule-based tools consistently miss.
The Dual-Edged Risk Anthropic Acknowledged
Anthropic made a direct and deliberate admission in the launch announcement: the same capabilities that help defenders find and fix vulnerabilities could help attackers exploit them. This acknowledgment is not a disclaimer it frames the entire rationale for launching the tool as a limited research preview rather than a general release.
The company’s stated goal is to put this power squarely in the hands of defenders and protect code against what it describes as “this new category of AI-enabled attack.” Its logic: attackers will use AI to find exploitable weaknesses faster than ever, but defenders who move quickly can find those same weaknesses, patch them, and reduce the risk of attack first. Bloomberg reported that cybersecurity software stocks declined on February 20, 2026, the day of Anthropic’s announcement, as investors interpreted the tool as a competitive threat to established security software vendors.
Who Can Access Claude Code Security Right Now
The tool is available now as a limited research preview not a general release. Anthropic’s stated reason: to work together with participants to refine capabilities and ensure responsible deployment before wider access.
Current access pathways:
- Enterprise customers available now via Claude Code on the web
- Team customers available now via Claude Code on the web
- Open-source maintainers free, expedited access; apply at claude.com/contact-sales/security
- General availability date not announced
Preview participants get early access and collaborate directly with Anthropic’s team to refine the tool.
Who can access Claude Code Security in 2026?
Claude Code Security is available in a limited research preview for Anthropic’s Enterprise and Team customers. Open-source repository maintainers can apply for free, expedited access at claude.com/contact-sales/security. General availability timing has not been announced. Preview participants work directly with Anthropic’s team to refine the tool’s capabilities.
Limitations and Considerations
Claude Code Security performs static reasoning on source code. It does not test running applications, simulate live attack scenarios, or replace dynamic testing, penetration testing, or formal threat modeling. The mandatory human-in-the-loop architecture where developers approve every fix keeps teams in full control but limits throughput for organizations managing large vulnerability backlogs, as there is no auto-remediation pathway at any access tier. Independent benchmark performance data across specific programming languages, framework types, and codebase sizes has not been published as of February 2026.
Can Claude Code Security replace human security researchers?
No. Claude Code Security identifies vulnerabilities and suggests patches, but every finding requires explicit human review and approval before any fix is applied. Anthropic designed it to augment security teams by reducing backlogs and detecting complex bugs it does not replace dynamic analysis, penetration testing, red team exercises, or formal threat modeling of live applications.
What This Means for Security Teams in 2026
Anthropic expects that a significant share of the world’s code will be scanned by AI in the near future, given how effective models have become at finding long-hidden bugs and security issues. The strategic implication is concrete: AI can now detect classes of vulnerabilities, complex business logic flaws, multi-component broken access control, subtle data flow issues that had gone undetected for decades despite active expert review.
For teams currently running rule-based static analysis pipelines, Claude Code Security is best approached as a complementary reasoning layer adding detection depth for complex and novel vulnerability classes while existing tools handle documented pattern coverage and CI/CD pipeline speed.
Frequently Asked Questions (FAQs)
What is Claude Code Security?
Claude Code Security is a new capability built into Claude Code on the web, available in a limited research preview as of February 20, 2026. It scans codebases for security vulnerabilities and suggests targeted patches for human review, designed to find complex vulnerabilities that traditional rule-based tools typically miss.
How does Claude Code Security differ from traditional security tools?
Traditional static analysis tools are rule-based and match code against known patterns effective for documented issues like exposed passwords, but unable to detect context-dependent vulnerabilities like business logic flaws or broken access control. Claude Code Security reads and reasons through code like a human researcher, tracing data flows and understanding component interactions without relying on predefined rules.
Who can access Claude Code Security right now?
Access is limited to Enterprise and Team customers on Claude Code on the web, plus open-source maintainers who can apply for free, expedited access at claude.com/contact-sales/security. Participants work directly with Anthropic’s team during the preview period. General availability has not been announced.
Does Claude Code Security apply patches automatically?
No. Nothing is applied without human approval. The tool identifies vulnerabilities, runs a multi-stage adversarial verification pass, assigns severity and confidence ratings, and presents suggested patches in the dashboard but developers make every remediation decision without exception.
Which AI model powers Claude Code Security?
Claude Code Security runs on Claude Opus 4.6. Using this model, Anthropic’s Frontier Red Team found over 500 vulnerabilities in production open-source codebases bugs that had gone undetected for decades despite years of expert review.
Can it replace human security researchers or penetration testers?
No. The tool performs static reasoning on source code it does not simulate live attacks, test running applications, or replicate the adversarial creativity of human red teams. Anthropic designed it to work alongside security teams, reducing vulnerability backlogs by handling complex static code analysis.
Did cybersecurity stocks react to this announcement?
Yes. Bloomberg reported cybersecurity software stocks declined on February 20, 2026, the day of Anthropic’s announcement, with investors interpreting the tool as a competitive threat to established security software vendors.
Is Claude Code Security safe for proprietary codebases?
Anthropic built the tool for Enterprise and Team use. Organizations with sensitive or regulated codebases should review Anthropic’s enterprise data processing terms at trust.anthropic.com before submitting proprietary code.