Quick Brief
- Cursor’s sandboxed agents interrupt developers 40% less, saving hours of manual review
- macOS uses Apple’s deprecated-but-active Seatbelt (sandbox-exec); Linux uses Landlock and seccomp
- Windows runs the Linux sandbox inside WSL2 until native developer-grade primitives are available
- NVIDIA is a confirmed enterprise customer fully onboarded onto Cursor’s sandbox system
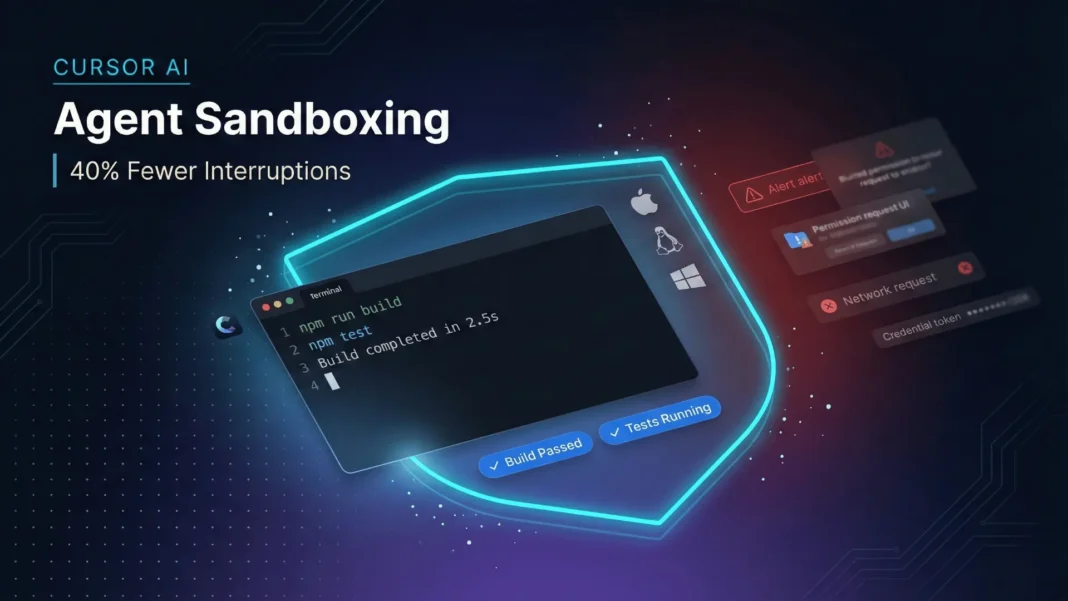
Most developers don’t realize their AI coding agent has near-unrestricted access to their terminal until something breaks. Cursor’s agent sandboxing system, rolled out across macOS, Linux, and Windows in early 2026, changes that equation directly: sandboxed agents run freely inside controlled boundaries and surface permission requests only when they need to step outside most often for internet access. This analysis breaks down the technical architecture, platform-specific implementation, and what the design choices mean for developers and enterprise security teams running agents at scale.
Why Unrestricted Agents Create Silent Risk
Every time a developer clicks “approve” on an AI terminal command without reading it carefully, they trade security for speed. Cursor’s engineering team identified this pattern as approval fatigue, a failure mode that compounds as engineers run multiple agents in parallel and must context-switch between accumulating approval prompts. The mechanism meant to protect developers becomes a reflex rather than a checkpoint.
The stakes are concrete. An unchecked agent can delete databases, ship broken code, or leak secrets. Per NVIDIA AI Red Team Principal Security Architect Rich Harang’s January 2026 security guidance, developer machines commonly contain API keys in environment variables, credentials in ~/.aws, tokens in .env files, and SSH keys all potentially in scope for an agent with unrestricted filesystem access.
What is approval fatigue in AI coding?
Approval fatigue occurs when developers stop reviewing AI agent command prompts carefully due to their volume. As agents run tasks in parallel, approvals accumulate faster than engineers can inspect them, effectively disabling the security checkpoint they were built to provide. Cursor’s sandboxing was designed specifically to eliminate this failure mode.
How the Sandbox Architecture Solves This
Cursor’s solution is a uniform sandbox API that confines agents inside a controlled environment. Agents execute builds, run tests, explore the filesystem, and make changes without interrupting the developer but must request explicit elevated permissions before reaching outside the sandbox, primarily for network access.
The result is measurable: sandboxed agents stop 40% less often than unsandboxed agents, according to Cursor’s own production data. As of February 2026, one third of all requests on supported platforms run with the sandbox active, and Cursor has onboarded many enterprise customers including NVIDIA.
How does Cursor AI agent sandboxing reduce interruptions?
Cursor’s sandbox lets agents execute terminal commands freely within a controlled filesystem environment without triggering developer approval prompts. Agents request elevated permissions only when stepping outside the sandbox primarily for internet access. This reduces agent interruptions by 40% compared to unsandboxed workflows, according to Cursor’s February 2026 production data.
Platform-by-Platform Implementation
Cursor’s sandbox looks different on each OS because macOS, Linux, and Windows expose fundamentally different kernel-level primitives. The engineering team Ani Betts, Yash Gaitonde, and Alex Haugland made distinct architectural choices on each platform rather than forcing a single mechanism across all three.
macOS: Seatbelt’s Unexpected Revival
Cursor evaluated four sandboxing approaches on macOS before choosing Seatbelt: App Sandbox, containers, virtual machines, and Seatbelt itself. App Sandbox would require signing every binary an agent might execute adding significant complexity and opening new abuse vectors through agent-generated binaries inheriting Cursor’s trust. Containers limit execution to Linux binaries. Virtual machines impose unacceptable startup latency and memory overhead.
Seatbelt, accessed via sandbox-exec, was introduced in 2007 and deprecated in 2016, but remains in active use by critical applications including Chrome. It allows a command to run under a sandbox profile that constrains the behavior of an entire subprocess tree, restricting syscalls and read/write access to specific files and directories through a policy language. Cursor generates this policy dynamically at runtime from workspace-level settings, admin-level settings, and the user’s .cursorignore file.
Linux: Landlock and Seccomp Directly Composed
Linux exposes the required primitives via Landlock and seccomp, but leaves userspace responsible for composing them into a working sandbox. Several open-source projects combine these mechanisms, but none support .cursorignore integration so Cursor built directly on the primitives.
Seccomp blocks unsafe syscalls at the kernel level; Landlock enforces filesystem restrictions, making ignored files completely inaccessible to the sandboxed process. Cursor maps user workspaces into an overlay filesystem and overwrites ignored files with Landlocked copies that cannot be read or modified. Finding and remounting those files is the slowest initialization step Linux does not expose file paths easily in a seccomp-bpf context, preventing the lazy-filtering approach macOS uses via Seatbelt.
Windows: WSL2 as an Engineering Bridge
On Windows, Cursor runs its Linux sandbox inside WSL2. Most existing Windows sandboxing primitives are designed for browsers and do not support general-purpose developer tools. Cursor is working directly with Microsoft to ensure the necessary primitives become available for a native Windows implementation.
| Platform | Mechanism | Key Technical Constraint | Shipping Status |
|---|---|---|---|
| macOS | Seatbelt / sandbox-exec | Dynamic policy generated at runtime via .cursorignore |
Shipped |
| Linux | Landlock + seccomp | Overlay filesystem remounting slowest init step | Shipped |
| Windows | WSL2 (Linux sandbox bridge) | No native dev-tool primitives yet; working with Microsoft | Shipped via WSL2 |
Teaching the Agent to Understand Its Own Limits
A sandbox is only effective if the agent can anticipate which commands will succeed inside it and recognize when escalation is needed. Cursor addressed this through targeted changes to the agent harness, not just the sandbox infrastructure itself.
The team updated Shell tool descriptions to communicate sandbox constraints directly to the model: which filesystem paths are accessible, whether git or network access is permitted based on user settings, and how to request elevated permissions when a blocked operation is necessary. Getting a baseline prompt change that worked reliably required extensive manual testing running common development rollouts, observing unexpected failures, adjusting the prompt, and repeating the cycle.
Why do AI agents need to be sandbox-aware?
Without explicit awareness of sandbox constraints, AI coding agents retry blocked terminal commands repeatedly without requesting elevated permissions burning tokens and time. Cursor resolved this by updating Shell tool result rendering to surface the specific sandbox restriction causing each failure and recommend appropriate escalation in certain cases. This significantly improved both Cursor Bench benchmark scores and production reliability.
Changes were evaluated using Cursor’s internal benchmark, Cursor Bench, comparing agents with and without sandboxing enabled. The most common early failure mode was the agent repeatedly retrying the same terminal command without changing permissions. After shipping updated Shell tool result rendering explicitly labeling the sandbox constraint and suggesting escalation in specific cases agents recovered far more gracefully from sandbox-related failures and offline eval performance improved significantly.
Security Risks That Remain After Sandboxing
Sandboxing substantially reduces blast radius but does not close every risk vector. NVIDIA AI Red Team Principal Security Architect Rich Harang published mandatory and recommended controls in January 2026 that address five residual vulnerabilities even in sandboxed agentic systems:
- Malicious hooks or local MCP initialization commands ingested during agent startup that run outside the sandbox context
- Kernel-level vulnerabilities that can lead to sandbox escape macOS Seatbelt, Linux Landlock, and Docker all share the host kernel, leaving it exposed to arbitrary code execution
- Agent access to secrets developer machines commonly contain API keys,
.envtokens, and SSH keys that fall within sandbox read scope if not explicitly excluded - Failure modes in approval caching a single legitimate approval can open the door to future adversarial reuse if approvals are cached or persisted rather than required fresh each time
- Accumulation of secrets, IP, or exploitable code in long-running sandbox sessions
NVIDIA’s mandatory controls for all agentic deployments are: blocking network egress to arbitrary sites, blocking file writes outside the active workspace at OS level, and blocking all writes to agent configuration files regardless of user approval.
Considerations and Limitations
Cursor’s sandbox covers local agents on macOS, Linux, and Windows. The Seatbelt mechanism used on macOS is deprecated infrastructure, and future macOS OS-level changes could affect this approach. Windows native sandboxing remains dependent on Microsoft developing new primitives that are not yet publicly available. NVIDIA’s guidance notes that OS-level sandboxes like macOS Seatbelt, Linux solutions, and Docker all share the host kernel meaning kernel-level exploits remain a viable attack path without additional virtualization.
What This Means for Developers Running Agents Today
For individual developers, sandboxing enables auto-approve for routine agent tasks without exposing the full system. The 40% reduction in interruptions compounds across a workweek particularly for engineers running parallel agents on complex, multi-service codebases. Agents can now complete full build-test-lint cycles autonomously, escalating only when a network call or permission boundary is actually required.
For enterprise security teams, NVIDIA’s Red Team recommends three supplemental controls beyond Cursor’s built-in sandbox: requiring fresh manual approval for every action that violates default-deny isolation controls (never cached), using secret injection to scope credentials to the minimum required for each specific task rather than inheriting the full host credential set, and establishing lifecycle management controls to prevent accumulation of secrets, IP, or exploitable artifacts over time.
Is Cursor AI agent sandboxing safe for enterprise use?
Cursor’s agent sandboxing used by enterprise customers including NVIDIA provides meaningful OS-level security isolation on macOS, Linux, and Windows. NVIDIA’s AI Red Team January 2026 guidance recommends supplementing it with secret injection, network egress controls allowing only known-good locations, per-action manual approval without caching, and sandbox lifecycle management to prevent credential and IP accumulation.
The Architecture Cursor Is Building Toward
Cursor’s engineering team has stated their next capability target: sandbox-native agents trained with awareness of their execution constraints built in from the ground up. These agents would have the freedom to write and execute scripts directly rather than being limited to predefined tool-calling unlocking significantly more autonomous development capability within well-defined security boundaries.
NVIDIA’s January 2026 security guidance independently confirms this direction is necessary: application-level controls are insufficient for agentic tools that perform arbitrary code execution by design, because once control passes to a subprocess, the application has no visibility into or control over what it does. OS-level controls like macOS Seatbelt work beneath the application layer to cover every process in the sandbox regardless of how those processes start.
Frequently Asked Questions (FAQs)
What is Cursor AI agent sandboxing?
Cursor AI agent sandboxing is a security system that lets AI coding agents execute terminal commands freely inside a controlled environment. Agents request permission only when accessing resources outside the sandbox primarily the internet reducing total developer interruptions by 40% compared to unsandboxed workflows, per Cursor’s February 2026 production data.
Which platforms support Cursor’s agent sandbox?
Cursor’s agent sandbox ships on macOS using Seatbelt (sandbox-exec), Linux using Landlock and seccomp kernel primitives, and Windows via the Linux sandbox running inside WSL2. Cursor is working with Microsoft to build native Windows developer-focused sandboxing primitives for a future release.
How does Cursor prevent agents from reading sensitive files?
Cursor generates sandbox policies dynamically at runtime from workspace settings and .cursorignore rules. On Linux, ignored files are remounted as Landlocked copies the agent cannot read or modify. On macOS, Seatbelt profiles restrict read and write operations at the syscall level for each subprocess tree.
What security risks remain even with Cursor’s sandbox active?
NVIDIA’s AI Red Team identifies five residual risks: ingestion of malicious hooks running outside sandbox scope, kernel-level vulnerabilities enabling sandbox escape, agent access to secrets in filesystem scope, failure modes in approval caching, and accumulation of secrets in long-running sessions. NVIDIA recommends secret injection, network egress blocking, and sandbox lifecycle controls as mandatory supplements.
Why is Linux sandbox initialization slower than macOS?
Linux’s seccomp-bpf context does not easily expose file paths during active filesystem operations, blocking the lazy-filtering approach macOS uses via Seatbelt. Cursor must find and remount all workspace files into an overlay filesystem before sandboxing begins making initialization the slowest part of the Linux implementation.
Does sandboxing degrade Cursor agent task performance?
Post-update agents perform comparably to unsandboxed agents on Cursor’s internal benchmark, Cursor Bench. The early failure mode agents repeatedly retrying blocked commands without requesting escalation was resolved by updating Shell tool result rendering to explicitly surface sandbox constraints and recommend appropriate escalation actions.
What enterprises use Cursor’s sandboxed agents?
NVIDIA is the enterprise customer Cursor’s engineering team has publicly cited as fully onboarded onto the sandbox system. Cursor’s engineering post from February 18, 2026 states the team has “onboarded many enterprise customers such as NVIDIA”.
What are sandbox-native agents, and when are they coming?
Sandbox-native agents are Cursor’s next development target: models trained with built-in awareness of their execution boundaries rather than relying only on prompt-level constraints. Unlike current tool-calling agents, sandbox-native agents would write and execute scripts directly within defined limits. No public timeline has been disclosed by Cursor.